Apple Refines Zero-Reboot Security in iOS 26.3
Apple is fine-tuning a more seamless approach to device safety, stress-testing a revamped background security mechanism within the latest developer betas for iOS 26.3 and macOS Tahoe 26.3. This system applies critical protections silently, killing the need for full OS updates or the "Update Now" prompts that disrupt daily workflows.
While the "Background Security Improvements" framework first appeared in iOS 26.1 late last year, the 26.3 beta marks a significant maturation of the technology. By decoupling high-priority patches from the monolithic iOS release cycle, Apple is moving toward a "zero-friction" security model where the most dangerous vulnerabilities are neutralized before the user even knows they exist.
Silent Protection: Ending Reboot Fatigue
The mechanism targets specific, high-risk vectors like certificate blocklists and exploit mitigations. Unlike the older Rapid Security Response (RSR) system, which often felt like a "diet" version of a full update, these new payloads install without necessitating a system restart.
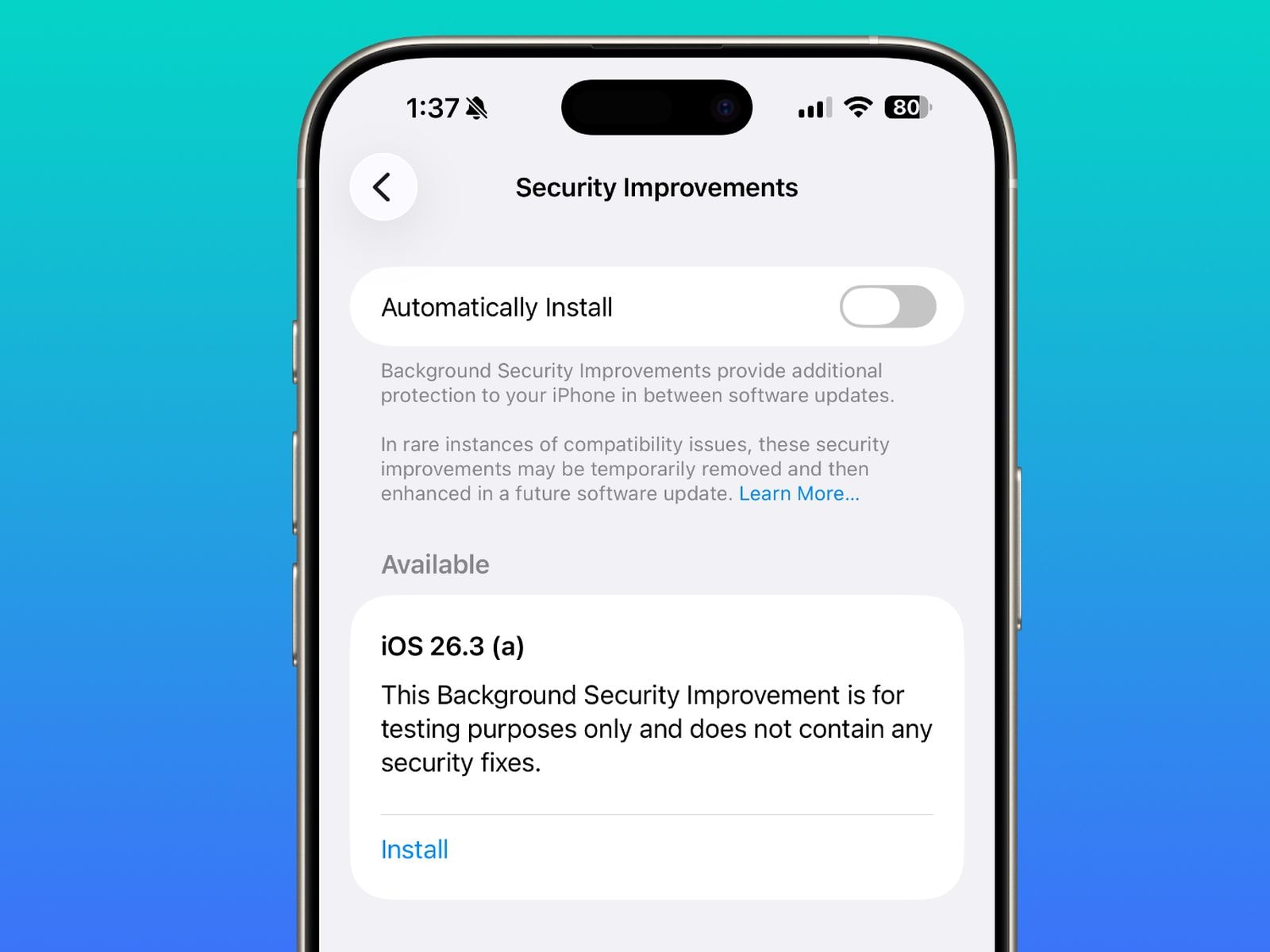
This shift addresses a long-standing pain point: reboot fatigue. In an era where users juggle dozens of open tabs and background processes, a 10-minute restart is a hurdle many delay for days. By delivering these fixes silently, Apple ensures the device's defensive posture remains current without forcing a productivity break. Users can still find the master toggle for this feature within the Automatic Updates section of System Settings, keeping the automation optional but encouraged.
The Audit Trail: Keeping Silent Updates Accountable
Automation shouldn't mean a lack of oversight. Apple is building this system to satisfy both the casual user and the enterprise administrator who requires a verifiable paper trail. Even when an update arrives silently, it leaves a footprint.
Any changes pushed via this background channel populate in system logs and the "About" section under System Reports. This transparency ensures that "silent" doesn't mean "secret." For security-conscious users, the ability to audit exactly when a mitigation was applied is crucial for maintaining trust in a system that acts on its own.
Outgrowing the RSR Era
This evolution mirrors Google’s "Project Mainline" on Android, which modularized core components to allow for faster, reboot-free updates via the Play Store. Apple is now applying that same logic to its walled garden, but with a more integrated execution.
The most visible change for long-time observers is the death of the clunky version suffixes. Under the old RSR system, users would see confusing version numbers like "iOS 26.1 (a)" or "(b)." This new background mechanism eliminates that UI clutter entirely. By the time a vulnerability is widely publicized, the mitigation is likely already active in the system's kernel or certificate store, pushed across the global install base in hours rather than weeks.
As this system matures through the 26.3 cycle, it signals the eventual sunset of the Rapid Security Response brand. We are moving toward a future where "updating" is no longer a manual chore for the user, but a continuous, invisible background process that treats security as a live service rather than a scheduled event.