1Password Updates Browser Protections to Block AI-Generated Phishing and Agentic Leaks
Standard password managers have historically relied on a simple URL-matching logic that is increasingly easy to bypass. As scammers use AI to generate "Punycode" attacks and lookalike domains that mirror legitimate sites with pixel-perfect accuracy, the manual process of verifying a URL has become a significant security bottleneck. In response, 1Password has rolled out a series of real-time safeguards designed to move the software from a passive database to an active gatekeeper at the point of entry.
This shift is driven by the escalating costs of credential theft. IBM’s latest reporting indicates that a single successful phishing breach now costs enterprises an average of $4.8 million. 1Password’s own data reveals a troubling success rate for these attacks: while 89% of Americans report being targeted by phishing, over 60% of those targeted have been successfully compromised. These figures suggest that human intuition is no longer a reliable defense against AI-scaled social engineering.
Intercepting the DOM: The New Credential "Kill Switch"
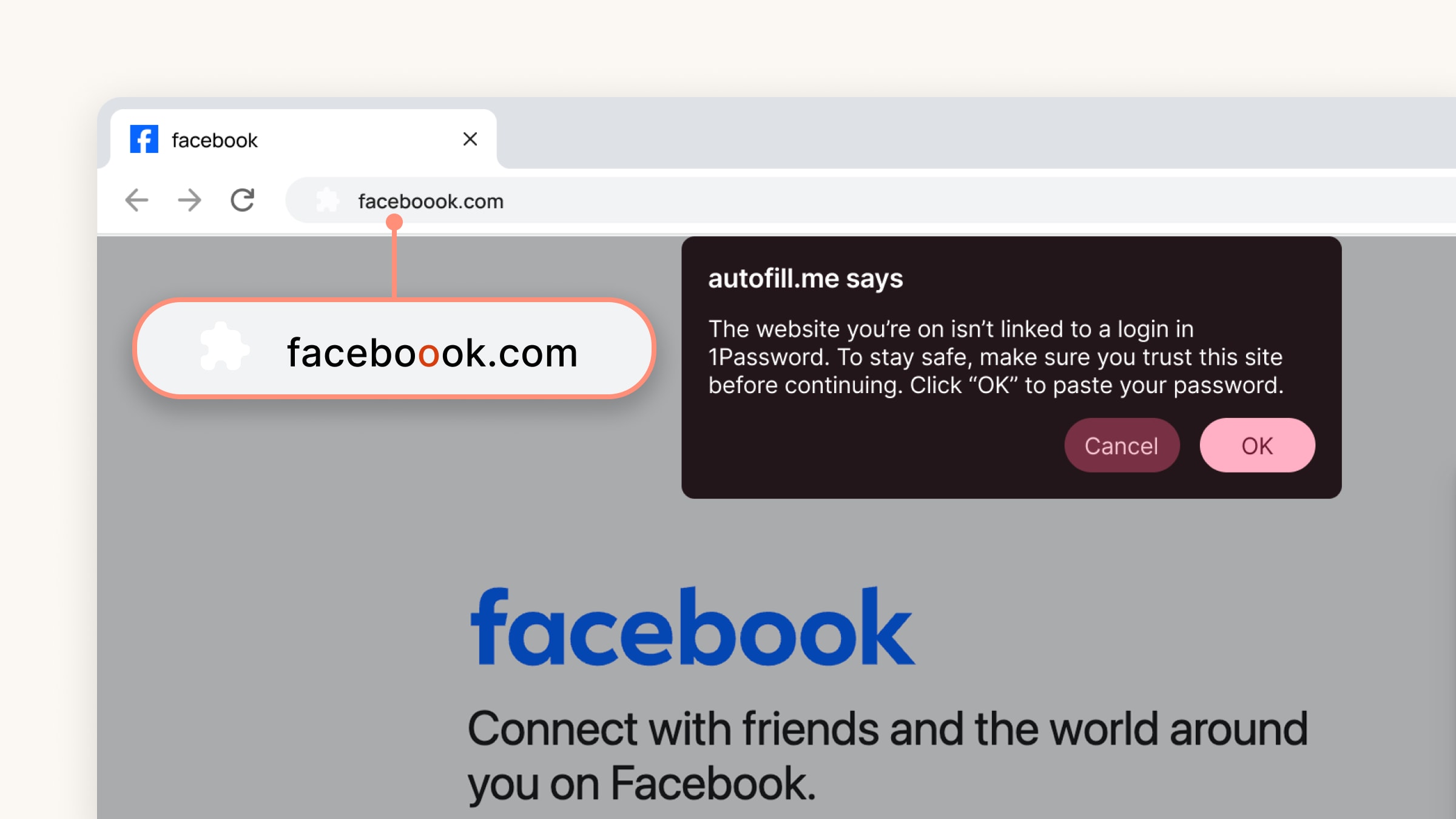
The updated defense mechanism changes how the 1Password browser extension interacts with a webpage's Document Object Model (DOM). Previously, the extension largely waited for a user to initiate an autofill request. Now, the extension proactively monitors the site's identity the moment the page loads. If the URL deviates from the saved vault entry—even by a single character or a hidden character set—1Password immediately disables the autofill function.
When this "kill switch" is triggered, the extension replaces the login fields with a high-visibility warning stating the site is unrecognized. This forces a manual review, preventing the accidental "one-click" submission of credentials to a malicious script.
However, this heightened security comes with a trade-off in user experience. Power users who frequently navigate complex enterprise Single Sign-On (SSO) flows or internal staging environments may find these persistent warnings create "alert fatigue." If users become accustomed to dismissing these modals to get their work done, the effectiveness of the protection could diminish. To counter this, 1Password has included administrative whitelisting for enterprise environments, though the feature remains on by default for all retail users.
Securing the Agentic AI Workflow
The risk of credential exposure has moved beyond the browser and into the "Agentic AI" space. As users deploy autonomous AI agents to perform tasks across the web, these agents often require access to sensitive accounts. Without a secure handshake, an agent tasked with "generating a summary of Q4 billing" could inadvertently leak a Stripe API key or a session token directly into an AI prompt or an insecure log.
To mitigate this, 1Password has partnered with Browserbase and Perplexity to launch "Secure Agentic Autofill." This system uses a zero-knowledge security model to inject credentials into a secure browsing environment at runtime. In practice, this means an AI agent can log into a service to pull a report, but the underlying "secret"—the actual password or key—is never visible to the AI model or the agent itself. It allows for automation without the risk of an LLM "hallucinating" or leaking private credentials into its training data or output.
Hardening the Development Environment
The threat surface is also expanding for software engineers through "IDEsaster" vulnerabilities. This class of attack targets AI agents embedded within Integrated Development Environments (IDEs), tricking them into executing malicious code or exposing environment variables.
1Password’s new integrations with tools like Cursor aim to bridge the gap between security and developer velocity. Through "Cursor Hooks" and "1Password Environments," sensitive .env files and API keys are no longer stored in plain text on a local machine. Instead, they are pulled from the 1Password vault only during authorized runtimes. This setup prevents AI-assisted coding tools from accidentally indexing secrets while ensuring that developers don't have to manually copy-paste keys, which remains one of the most common ways credentials are leaked to public repositories.